A new variant of the Flashback Trojan is using three methods to infect Macs, reports Intego.
The malware first tries to install itself using one of two Java vulnerabilities. If this is successful, users will be infected with no intervention. If these vulnerabilities are not available – if the Macs have Java up to date – then it attempts a third method of installation, trying to fool users through a social engineering trick. The applet displays a self-signed certificate, claiming to be issued by Apple. Most users won't understand what this means, and click on Continue to allow the installation to continue.
Flashback.G injects code into web browsers and network applications looking for usernames and passwords from domains such as Google, Yahoo, CNN, Paypal, banks, and others. Some infected applications such as Safari and Skype will consequently crash. This malware also has an automatic update module that checks for new versions.
Intego notes that their VirusBarrier X6 detects Flashback.G and all other variants of this Trojan horse. In this case, the mere presence of VirusBarrier X6 causes the malware's installer to abort, so even if users do not have VirusBarrier X6′s real-time scanner active, the Trojan will look elsewhere. You can fix the Java vulnerabilities by updating your OS X installation.
Read More [via 9to5Mac]
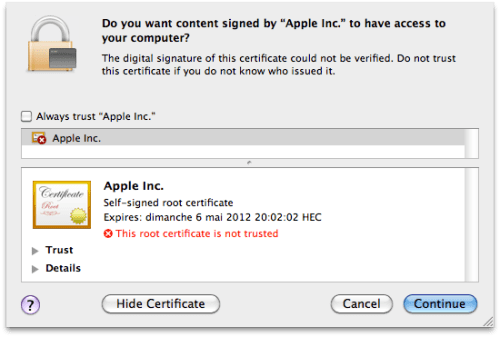

The malware first tries to install itself using one of two Java vulnerabilities. If this is successful, users will be infected with no intervention. If these vulnerabilities are not available – if the Macs have Java up to date – then it attempts a third method of installation, trying to fool users through a social engineering trick. The applet displays a self-signed certificate, claiming to be issued by Apple. Most users won't understand what this means, and click on Continue to allow the installation to continue.
Flashback.G injects code into web browsers and network applications looking for usernames and passwords from domains such as Google, Yahoo, CNN, Paypal, banks, and others. Some infected applications such as Safari and Skype will consequently crash. This malware also has an automatic update module that checks for new versions.
Intego notes that their VirusBarrier X6 detects Flashback.G and all other variants of this Trojan horse. In this case, the mere presence of VirusBarrier X6 causes the malware's installer to abort, so even if users do not have VirusBarrier X6′s real-time scanner active, the Trojan will look elsewhere. You can fix the Java vulnerabilities by updating your OS X installation.
Read More [via 9to5Mac]



