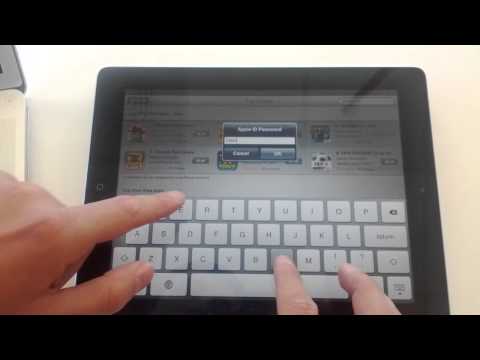
Apple recently turned on HTTPS for the App Store preventing a slew of possible attacks including password stealing, app swapping, fake app upgrades, app installation prevention, and privacy leaks.
Elie Bursztein of Google is credited with reporting the vulnerabilities to Apple, according to an Apple Web Server Notifications document posted two weeks ago.
2013-01-23 itunes.apple.com
Active content is now served over HTTPS by default. We would like to acknowledge Bernhard 'Bruhns' Brehm of Recurity Labs, Elie Bursztein of Google, and Rahul Iyer of Bejoi LLC for reporting this issue.
In a blog post yesterday Bursztein outlines and even demos the attacks that used to be possible.
● Password stealing: Trick the user into disclosing his or her password by using the application update notification mechanism to insert a fake prompt when the App Store is launched.
● App swapping: Force the user to install/buy the attacker’s app of choice instead of the one the user intended to install/buy. It is possible to swap a free app with a paid app.
● App fake upgrade: Trick the user into installing/buying the attacker’s app of choice by inserting fake app upgrades, or manipulating existing app upgrades.
● Preventing application installation: Prevent the user from installing/upgrading applications either by stripping the app out of the market or tricking the app into believing it is already installed.
● Privacy leak: The App Store application update mechanism discloses in the clear the list of the applications installed on the device.
Check out the video demos below or hit the link for details on each attack scenario, sample code, and more.
Read More [via Marcus]
Elie Bursztein of Google is credited with reporting the vulnerabilities to Apple, according to an Apple Web Server Notifications document posted two weeks ago.
2013-01-23 itunes.apple.com
Active content is now served over HTTPS by default. We would like to acknowledge Bernhard 'Bruhns' Brehm of Recurity Labs, Elie Bursztein of Google, and Rahul Iyer of Bejoi LLC for reporting this issue.
In a blog post yesterday Bursztein outlines and even demos the attacks that used to be possible.
● Password stealing: Trick the user into disclosing his or her password by using the application update notification mechanism to insert a fake prompt when the App Store is launched.
● App swapping: Force the user to install/buy the attacker’s app of choice instead of the one the user intended to install/buy. It is possible to swap a free app with a paid app.
● App fake upgrade: Trick the user into installing/buying the attacker’s app of choice by inserting fake app upgrades, or manipulating existing app upgrades.
● Preventing application installation: Prevent the user from installing/upgrading applications either by stripping the app out of the market or tricking the app into believing it is already installed.
● Privacy leak: The App Store application update mechanism discloses in the clear the list of the applications installed on the device.
Check out the video demos below or hit the link for details on each attack scenario, sample code, and more.
Read More [via Marcus]

![Apple Turns on HTTPS for App Store, Prevents Password and App Stealing [Video] Apple Turns on HTTPS for App Store, Prevents Password and App Stealing [Video]](/images/news/28061/109189/109189-64.png)