Macs older than one year are vulnerable to an exploit that can overwrite a machine's firmware, letting attackers control devices even after they are formatted or restored.
The vulnerability, discovered by OS X Security researcher Pedro Vilaca, target a machine's BIOS after it wakes from sleep. Normally, protection known as FLOCKDN, would prevent any apps write access to the BIOS region, but for some reason, the FLOCKDN protection is inactive after a Mac wakes from sleep. That leaves the operating system open to apps to reflash the BIOS and modify the extensive firmware interface (EFI).
"The bug can be used with a Safari or other remote vector to install an EFI rootkit without physical access," Vilaca said in his blog post. "The only requirement is that a suspended happened in the current session. I haven’t researched but you could probably force the suspend and trigger this, all remotely. That’s pretty epic ownage ;-)."
One installed, the malicious code would be very difficult to detect or delete, as reformatting or reinstalling the OS would do nothing since that does not reflash the BIOS. Unfortunately, there is not much users of vulnerable Macs can do to prevent the exploit until Apple releases a fix.
While Vilaca noted how serious this bug is, he did say that in theory, there is not too much to worry about. The bug is more likely to be applied as a targeted attack versus mass exploitation. Vilaca tested the bug on a MacBook Pro Retina, a MacBook Pro 8.2 and a MacBook Air, all running the latest available EFI firmware from Apple.
All Macs released since mid to late 2014 are not affected by this vulnerability, but Vilaca said he was not sure if Apple silently patched it or fixed it accidentally.
Read More via ArsTechnica
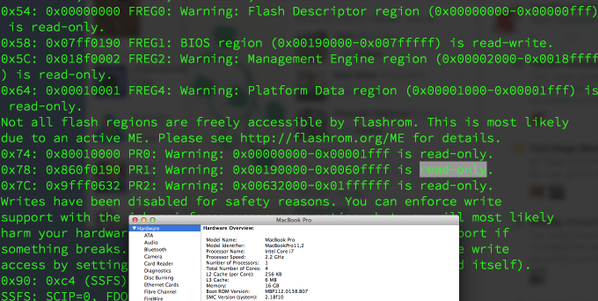

The vulnerability, discovered by OS X Security researcher Pedro Vilaca, target a machine's BIOS after it wakes from sleep. Normally, protection known as FLOCKDN, would prevent any apps write access to the BIOS region, but for some reason, the FLOCKDN protection is inactive after a Mac wakes from sleep. That leaves the operating system open to apps to reflash the BIOS and modify the extensive firmware interface (EFI).
"The bug can be used with a Safari or other remote vector to install an EFI rootkit without physical access," Vilaca said in his blog post. "The only requirement is that a suspended happened in the current session. I haven’t researched but you could probably force the suspend and trigger this, all remotely. That’s pretty epic ownage ;-)."
One installed, the malicious code would be very difficult to detect or delete, as reformatting or reinstalling the OS would do nothing since that does not reflash the BIOS. Unfortunately, there is not much users of vulnerable Macs can do to prevent the exploit until Apple releases a fix.
While Vilaca noted how serious this bug is, he did say that in theory, there is not too much to worry about. The bug is more likely to be applied as a targeted attack versus mass exploitation. Vilaca tested the bug on a MacBook Pro Retina, a MacBook Pro 8.2 and a MacBook Air, all running the latest available EFI firmware from Apple.
All Macs released since mid to late 2014 are not affected by this vulnerability, but Vilaca said he was not sure if Apple silently patched it or fixed it accidentally.
Read More via ArsTechnica



